Linux ransomware, once a rarity in the cybersecurity landscape, has evolved into a significant threat for organizations worldwide – especially as new variants like LockBit Linux ESXi use sophisticated techniques to evade detection.
In this post, we outline how to protect against ransomware on Linux systems, plus the most common variants and attack vectors to be aware of.
🛡️ Block Ransomware Before It Spreads
Traditional antivirus isn’t enough. Datto EDR uses advanced AI-driven detection to stop cyberattacks at the endpoint, before they take down your business.
Does Ransomware Affect Linux?
Yes, ransomware can and does infect Linux devices, including Linux servers, PCs and cloud infrastructure. It affects data storage and backups by encrypting files using the same similar methods that other ransomware variants use to attack Windows-based machines.
It’s a common misconception that only Windows systems are vulnerable to ransomware. While it’s true that more than 90% of ransomware attacks target Windows, the rise of Linux ransomware is cause for concern. In 2025, new and emerging threats from hacker groups like Gunra and Eldorado are increasingly targeting Linux machines.
What is Ransomware?
Ransomware is a form of malware that encrypts files on your computer systems, usually rendering them inoperable. Attacks come with a ransom, typically demanding a cryptocurrency payment in exchange for a decryption key to restore the files.
Linux ransomware specifically targets and infects machines running the Linux operating system, which today powers millions of devices, servers and cloud environments for companies worldwide.
Why is Linux Ransomware a Concern?
Any business using Linux, in any part of its infrastructure, is at risk of having its critical operations severely disrupted by Linux ransomware. Even if Linux is not running on your local hardware, chances are it may be powering part of your cloud architecture or web services, as recent Linux statistics show:
- Although Windows dominates the desktop market, Linux is the overwhelming favorite when it comes to servers and supercomputers. Linux runs on nearly 80% of web servers globally, according to SQ Magazine.
- Linux is the most common O/S for constrained, embedded and IoT devices in industries like energy and manufacturing.
- Linux powers most of the U.S. government and military networks, as well as U.S. financial systems.
- In 2025, Linux’s global market size was projected to hit $26.21 billion. Experts expect that figure to grow to $99 billion by 2032.
- In 2021, 47% of software development occurred on Linux-based systems.
- There was a staggering 62% increase in ransomware attacks targeting Linux systems between Q1 2022 and Q1 2023.
The Rise of Ransomware on Linux
Ransomware on Linux systems is not new – successful attacks have been occurring for years. However, as attackers adapt their techniques, it has become even more important for businesses to deploy robust Linux ransomware protection.
In August 2022, for example, a ransomware attack on the government of Chile revealed that the infection targeted both Windows and Linux-based systems. More recently, attacks have used new variants of Gunra, SEXi/ESXi and Mallox ransomware (formerly known as TargetCompany, Mawahelper and Fargo) to target Linux machines. Jump below to see a fuller list of recent variants.
How is Linux Ransomware Different from Windows Ransomware?
The fundamental objective of Linux ransomware and Windows ransomware is the same. However, because they are often used for different purposes, there is some variation in how the attacks play out.
Vulnerabilities
According to a study by Verizon, 82% of data breaches involved the human element, including errors and misconfiguration. This has long been an issue for Windows systems, where phishing emails and stolen credentials give cyber attackers easy access to data.
Because Linux is less popular as a desktop operating system and many Linux users are technology professionals, ransomware gangs tend to look for different points of attack. Rather than relying on emails, they often search for vulnerabilities, such as out-of-date patches, and use them to gain entrance to Linux systems.
Double Extortion
Ransomware Linux attacks are often more complex and go after larger enterprises, which means that the criminals behind them might look for bigger payouts. While double extortion schemes exist in the world of Windows, they are especially common in Linux ransomware attacks.
In these scenarios, criminals will threaten not only to keep the data encrypted but also to leak it online. This places additional pressure on businesses that could be permanently damaged by the release of sensitive client, customer, employee or company data.
How Does Linux Ransomware Work?
Linux ransomware works in much the same way as ransomware infections on other systems such as Windows. Once a cybercriminal identifies a target, they find ways to exploit vulnerabilities and infect systems.
Attack Steps
There is no one-size-fits-all description of the ransomware process, but the essential stages are generally the same. During an attack, ransomware typically:
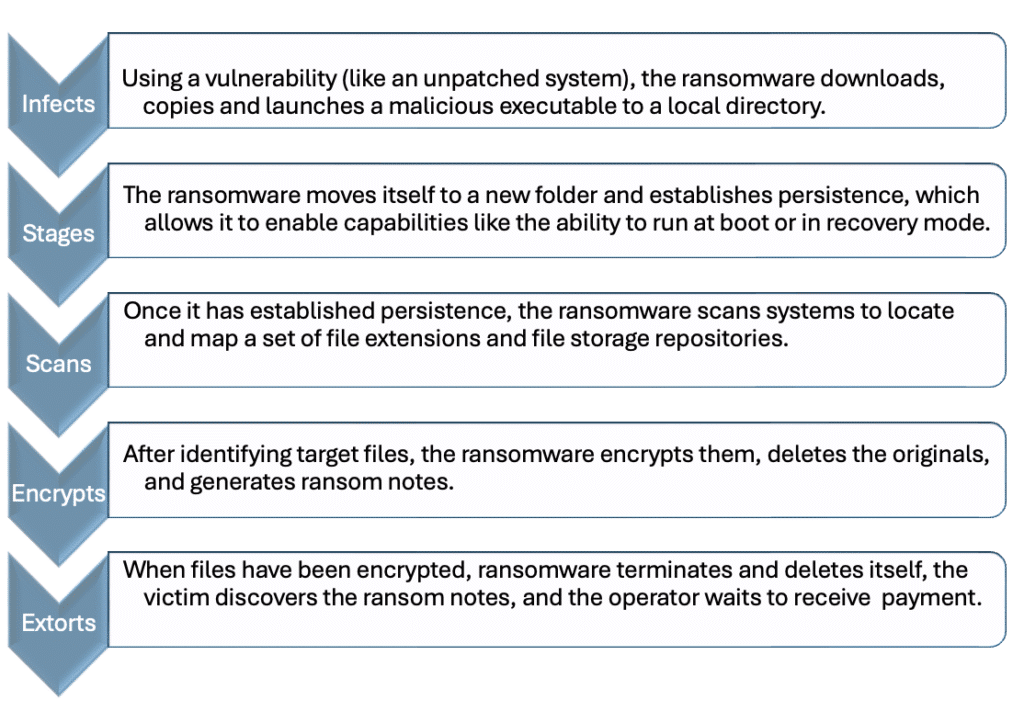
When the ransomware encrypts files and makes the ransom demand, the victim is left with no choice but to pay the ransom (which, for the record, is almost never advisable) or restore data from a backup.
Examples of Linux Ransomware
To get a better picture of how Linux ransomware operates, let’s explore three types that have emerged as significant threats in the past few years.
LockBit
LockBit is one of the most prominent families of Windows ransomware. In October 2021, experts began detecting cases of LockBit ransomware on Linux systems. Today, numerous LockBit variants target Linux, including a powerful encryptor that targets VMware ESXi servers.
LockBit uses a combination of Advanced Encryption Standard (AES) and elliptic-curve cryptography (ECC) algorithms for data encryption. It has the capability to log:
- Processor information
- Volumes in the system
- Virtual machines for skipping
- Encrypted files and total files
- Encrypted virtual machines and total virtual machines
- Total encrypted size
The LockBit variant contains the commands necessary to take several harmful steps, including suspending virtual machines, checking the status of data storage and disabling autostart. Once the ransomware infection is installed, LockBit demands a ransom and threatens to release data if their demands are not met.
Gunra
Emerging in April 2025, the Gunra ransomware group deployed a Linux variant after initially targeting Windows systems with a variant that bore similarities to Conti ransomware. The Gunra Linux ransomware variant is noteworthy for its efficiency: it’s capable of running up to 100 encryption threads in parallel – so it can infect a wide swath of data very quickly. It has been observed targeting various sectors, including manufacturing, healthcare and IT.
SEXi
Similar in targeting to Lockbit’s ESXi ransomware, SEXi is another potent malware variant specifically designed to attack and encrypt Linux-based VMware ESXi servers. Emerging in early 2024, its name is a play on its primary target, ESXi, a hypervisor that is fundamental to the virtualized infrastructure of many organizations and data centers. The ransomware encrypts files associated with virtual machines, such as virtual disks (.vmdk), storage, and backup images, appending the .SEXi extension to the filenames.
Cheerscrypt
In 2022, cybersecurity experts detected a new ransomware variant known as Cheerscrypt, a derivative of the Babuk malware family that targets ESXi servers. Many enterprises use ESXi, making it a logical target for cyberattacks. Unfortunately, the widespread use of ESXi means that successful attacks could cripple the operations of important services and infrastructure. Once it has been executed, Cheerscrypt terminates virtual machine processes with specific extensions: .log, .vmdk, .vmem, .vswp, and .vmsn.
This enables it to encrypt files with a .Cheers extension. As with many other Linux ransomware attacks, Cheerscrypt is a double extortion scheme that demands payment for data restoration and to prevent leaks. For each directory that is encrypted, a ransom note will appear.
AvosLocker
Another form of ransomware that targets ESXi servers is AvosLocker. Although it previously only targeted Windows, in 2022, AvosLocker became capable of encrypting Linux systems as well. Once it is launched, AvosLocker terminates ESXi machines and adds the extension .avoslinux to encrypted files.
Ransom notes generated by AvosLocker warn victims against shutting down their computers and provide a link to receive more information about paying the demanded ransom. According to Bleeping Computer, AvosLocker has issued a $1 million ransom demand to at least one victim.
What are the Most Common Types of Linux Ransomware?
New variants and types of ransomware are constantly under development, which can make it a challenge for security experts to track and prevent them. Monitoring has revealed several kinds of ransomware that have infected Linux systems in the past several years.
Some of the most common types of Linux ransomware, in addition to those listed above, include:
| Play | created a new stealthy Linux variant in 2024 designed to specifically target and encrypt VMware ESXi environments, a common target for other variants used by SEXi and LockBit ransomware |
| Mallox | previously known to breach Windows MS-SQL servers, was updated in 2024 to target Linux devices via a custom Python script |
| RansomEXX | also known as Defrat777, has attacked targets including the Texas Department of Transportation, Tyler Technologies and the Brazilian government. |
| Hive | sophisticated Linux ransomware that targets ESXi platforms |
| Revil | operates as ransomware-as-a-service (RaaS) and has attacked organizations like National Western Life and Erecat, began targeting Linux systems in 2021 |
| Mespinoza | also known as PYSA, developed a Linux variant in 2020 |
| DarkSide | one of the most threatening types of ransomware and targets both Windows and Linux systems in business, government and finance organizations around the world |
| HelloKitty | expanded into Linux ransomware and began attacking VMware ESXi servers and virtual machines in 2021 |
| Tycoon | ransomware has targeted higher education institutions, software companies and other businesses |
| Erebus | infamous for its 2017 attack against a web hosting company in South Korea and the $1 million Bitcoin payout that the business agreed to pay |
| QNAPCrypt | emerged in 2019 and targets network-attached storage Linux devices |
| KillDisk | targeted Linux since 2017 and makes it impossible for the target system to boot |
| SFile or Escal | first emerged in February 2020 as a threat to Windows systems, but it has since been ported to encrypt files on Linux systems |
What Linux Devices are Under Attack by Ransomware?
Given the right conditions, ransomware can infect nearly any Linux device. However, some of the most common devices under attack by Linux ransomware are web servers, VMware ESXi environments, PCs and network storage devices.
Cybersecurity experts have also reported a rise in ransomware attacks targeting Internet-connected devices (also known as IoT or Internet of Things) running on Linux. In late 2023, security firm Kaspersky warned of a sophisticated threat named NKAbuse, which uses the NKN blockchain-based network protocol to hide in Linux and IoT devices. This malware can be leveraged as a “flooder” – to carry out attacks like DDoS – as well as a backdoor to deliver other Linux malware payloads.
So while an infected IoT device may not seem dangerous on the surface, it’s a prime example of how Linux devices can be compromised to cause serious operational disruptions and lay the groundwork for larger ransomware attacks.
Linux Malware: Other Threats & Attack Vectors
Does ransomware affect Linux? Absolutely – but ransomware isn’t the only threat that companies must guard against. There are numerous other types of Linux malware, which include most of the same threats that target Windows systems, such as:
- Virus
- Trojans
- Worms
- Botnets
- Infected web scripts / web shells
- Fileless attacks
Keep in mind that Linux systems are also vulnerable to the wide array of attacks that prey on user error or deception, such as weak passwords, social engineering, brute-force attacks and outdated/unpatched software.
Internet of Things Devices
In addition to servers and cloud services, Linux is also the force that powers many IoT devices, such as smart devices, security systems and motion detectors. The ubiquitous nature of IoT devices has made them a primary target for Linux malware. Infecting these devices can give cybercriminals the opportunity to access networks, crash systems and use them for distributed denial of service (DDoS) attacks. There was a 77% increase in IoT malware from 2021 to the first half of 2022.
Cryptojacking
Cryptojacking occurs when bad actors take over devices to illegally mine for cryptocurrency. The criminals attempt to act in secret, without the device owner realizing that the attack has occurred, which distinguishes this type of crime from others like ransomware. In the first half of 2022, there were 66.7 million cryptojacking attacks, a 30% increase over the prior year. Much like ransomware, cryptojacking software has become a significant risk to Linux-based systems.
Linux Malware Families
According to a report from CrowdStrike, three Linux malware families have been particularly prominent in recent years:
- XorDDoS
- Mozi
- Mirai
XorDDoS is a Linux trojan that uses SSH brute-forcing attacks to gain control over devices. The number of XorDDoS samples increased by 123% from 2020 to 2021.
Similarly, Mozi, a peer-to-peer botnet network, was 10 times more common in 2021 compared to 2020. It also uses brute-force attacks on SSH ports and prevents their malicious software from being overwritten.
The last major Linux malware player in recent years has been Mirai, which takes advantage of vulnerable protocols and passwords to attack devices. There have been multiple variants of Mirai, including Sora, IZIH9 and Rekai. According to CrowdStrike, the prevalence of Mirai variants increased by up to 83% from 2020 to 2021.
Case Study: Linux Malware Attack
In March 2024, cybersecurity firm Cado Security warned of a new cryptojacking attack in which misconfigured Linux servers were targeted with Linux malware. As reported by SecurityWeek, the cryptojacking campaign used new Linux malware payloads to target misconfigured Apache Hadoop, Confluence, Docker and Redis instances. Attackers employed multiple Golang payloads to “automate the discovery and exploitation of vulnerable hosts, as well as a reverse shell and multiple user-mode rootkits to hide their presence.”
More alarmingly, attackers used a command to spawn a new container and created a bind mount for the Linux server’s root directory. This allowed them to write an executable that established a connection to the attackers’ command-and-control servers, through which the payload was delivered. Additional shell scripts were deployed to deliver additional payloads, delete shell history, disable SELinux and uninstall monitoring agents.
Linux Ransomware Protection: Tools & Best Practices
Linux ransomware protection requires a multilayered cybersecurity strategy. Below, we outline the essential security tools you should deploy for active defense and the critical best practices that can significantly reduce the risk of your Linus infrastructure being compromised.
1. Minimize the Risk of the Human Element
Although phishing is not the most common attack vector for Linux ransomware, it’s nevertheless essential that every member of your team receives comprehensive training on how to approach cybersecurity. Ensure that employees know how to watch for malicious links, enforce strict password requirements and ensure that the members of your IT team are regularly updating and installing patches.
- Implement security awareness training for all employees.
- Consider automated platforms for security training and phishing simulation exercises such as BullPhish ID, which can test employees on what they’ve learned. (See BullPhish ID pricing.)
2. Deploy Robust Backup & Disaster Recovery Solutions
Perhaps the most important step you can take to protect your business from the threat of ransomware (Linux or not) is to implement high-quality data backups, business continuity and disaster recovery solutions. Here’s what to look for:
- Ransomware detection: Look for solutions that actively detect ransomware in your data backups, such as the Datto SIRIS, which can alert you to the first signs of an infection, allowing you to quickly revert back to a clean recovery point. (See SIRIS models and pricing for more information.)
- Hybrid cloud: By storing backups both locally and in the cloud, you maintain quick access to your data and keep it safe from disruptions that occur on-site.
- Instant virtualization: Backups that are image-based, fully bootable virtual machines offer greater protection if your server fails. You can virtualize your protected systems in seconds.
- Faster, more resilient backups: Solutions with features like Inverse Chain Technology (Datto) let you schedule backups as frequently as every five minutes. This process also eliminates the typical lengthy rebuild process, where problems commonly occur with traditional incremental backups.
- Screenshot verification: Screenshots verify that your backups are bootable, so you never have to worry about getting a 3 a.m. wake-up call.
3. Automate Cybersecurity with MDR
MDR (Managed Detection and Response) can protect Linux systems from ransomware by providing continuous threat detection and expert-led remediation. Instead of blocking only known malware, MDR solutions focus on detecting and responding to suspicious behaviors that attackers use during a ransomware campaign. This 360-degree defense typically includes:
- Behavioral threat detection to identify early warning signs of a ransomware attack.
- Rapid response & containment on threats.
- Guided remediation backed by human intelligence.
Our recommended solution is RocketCyber MDR, which provides advanced threat protection for a variety of environments and Linux distributions. (Request RocketCyber pricing here.)
4. Plan Your Response in Advance
In order to maximize the chance that your business will survive a ransomware attack, it’s vital that you plan ahead. There are many steps you can take to prevent and recover from an attack, such as:
- Filtering suspicious email, attachments and links
- Limiting access and privileges
- Regularly patching devices
- Establishing firewalls
- Installing robust anti-malware
- Recovering data from a backup (rather than paying a ransom)
- Developing a comprehensive disaster recovery plan
When you have a strong disaster recovery plan in place, you can respond more effectively if an attack occurs.
Conclusion
The continued rise and evolution of Linux ransomware shows that no operating system is immune to attack. To protect your company, it is crucial to implement a multi-layered Linux ransomware protection and recovery strategy that includes employee training, robust cybersecurity and data backups across all your IT environments: on-premise and in the cloud.
How Can Businesses Protect Against Linux Ransomware?
To learn more about backup solutions and security tools for robust Linux ransomware protection, contact our business continuity experts at Invenio IT. Schedule a meeting today or contact us by calling (646) 395-1170 or by emailing success@invenioIT.com.





